For cheap and excellent services to buy vpn . Applications stumbling into a VPN may accordingly profit by the usefulness, security, and the board of the private system. Encryption is typical, even though not an innate, some portion of a VPN connection. VPN innovation was created to give corporate applications and assets to far off or versatile clients and to branch workplaces. For security, the private system association might set up utilizing an encoded layered burrowing convention, and clients might be required to pass different validation techniques to access the VPN. A few sites, notwithstanding, square access to known VPN innovation to forestall the circumvention of their geo-limitations. Numerous VPN suppliers have been creating methodologies to get around these bars.
A VPN is generally created by building up a virtual highlight point association using devoted circuits or burrowing conventions over existing systems. A VPN accessible from the open Internet can give a portion of the advantages of a broad zone arrange (WAN). From a client’s point of view, the assets accessible inside the private system can get to remotely.
Types Edit

VPN characterization dependent on the geography first, at that point on the innovation utilized.
A regular site-to-site VPN. New information systems permitted VPN-style associations with far off locales through dial-up modem or through rented line associations using X.25, Frame Relay, and Asynchronous Transfer Mode (ATM) virtual circuits gave through systems claimed and worked by media transmission transporters. These systems are not viewed as evident VPNs because they latently secure the information will communicate by making sensible information streams. They have been supplanted by VPNs dependent on IP and IP/Multi-convention Label Switching (MPLS) Networks, because of noteworthy cost-decreases and expanded bandwidth gave by new advances, for example, computerized supporter line (DSL) and fibre-optic systems.
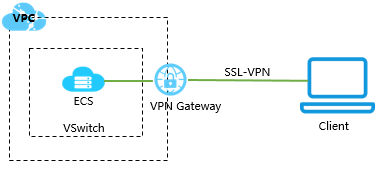
VPNs can be described as host-to-network or far off access by interfacing a single PC to a system or site-to-site to associate two systems. In a corporate setting, remote-access VPNs permit workers to get to the organization’s intranet outside the workplace. Site-to-site VPNs allow teammates in topographically divergent workplaces to have the equivalent virtual system. A VPN can likewise utilize to interconnect two comparable systems over a different halfway system, such as two IPv6 systems associated over an IPv4 network.
VPN frameworks might be arranged by:
- The burrowing convention used to burrow the traffic.
- the passage’s endpoint area, e.g., on the client edge or system supplier edge
- the sort of geography of associations, for example, site-to-site or system to-organize
- the degrees of security gave
- the OSI layer they present to the interfacing system, for example, Layer 2 circuits or Layer 3 system availability
- the number of concurrent associations
Secure Shell (SSH) VPN – OpenSSH offers VPN burrowing (particular from port sending) to tie down far off associations with a system or between organizing joins. OpenSSH worker gives a predetermined number of simultaneous passages. The VPN highlight itself doesn’t bolster individual authentication.
WireGuard is a convention. In 2020, WireGuard support was added to both the Linux and Android parts, freeing it from selection by VPN suppliers. Of course, WireGuard uses Curve25519 for crucial trade and ChaCha20 for encryption, yet additionally incorporates the capacity to pre-share a symmetric key between the customer and worker.
Passage endpoints must be verified before secure VPN passages can be built up. The client made far off access to VPNs that may utilize passwords, biometrics, two-factor validation, or other cryptographic strategies. System to-arrange burrows regularly use passwords or computerized authentications. They forever store the way to permit the passage to set up, consequently, without mediation from the executive.